A look at using Ultralytics YOLO models for AI threat detection
See how Ultralytics YOLO models power AI threat detection to uncover risks early, strengthen security awareness, and enable proactive prevention.
.webp)
See how Ultralytics YOLO models power AI threat detection to uncover risks early, strengthen security awareness, and enable proactive prevention.
.webp)
Across many industries, artificial intelligence (AI) is being adopted to improve security, boost efficiency, and create safer environments. In places like offices, factories, campuses, warehouses, and public spaces, achieving these goals depends on understanding what is happening in real time.
To support this, security cameras and smart surveillance systems are becoming increasingly common. However, simply collecting video footage isn't enough.
Traditional systems often rely on manual monitoring by human analysts or predefined rules, which makes it difficult to recognize early signs of risk. Interpreting large volumes of visual data in real time can be challenging, particularly in busy or dynamic settings.
This is where AI-driven threat detection becomes crucial. By analyzing live video streams, AI systems can identify patterns, behaviors, and situations that may indicate potential threats or potential attacks. In particular, computer vision is a branch of AI that enables these systems to understand visual information and turn raw footage into actionable insights.
With vision AI technology, organizations can move from reactive security measures to proactive prevention of emerging threats. In this article, we'll explore how AI threat detection works and how vision models like Ultralytics YOLO26 help surface risks earlier and support safer environments.
Before we dive into how AI improves threat detection, let’s first take a look at the challenges traditional threat detection systems face.
Most existing solutions rely on human oversight or signature-based tools, which detect threats by matching activity to known threats. This often requires security teams to monitor multiple camera feeds or dashboards at the same time to identify potentially unauthorized activity or deviations from normal activity.
In large facilities with hundreds of cameras, managing vast amounts of data quickly becomes difficult. As a result, certain activities may be overlooked, particularly in complex areas such as factory floors or restricted spaces like server rooms.
Another limitation is delayed responses. Traditional systems typically detect malicious activity only after an event has already occurred. While this works for confirming known concerns, it means not being able to respond early to threats.
This delay can make it harder to address situations where physical access, such as entry into a restricted server room, contributes to broader security concerns, including cyber threats and cyberattacks at data centers. AI-powered systems help reduce this gap by identifying vulnerabilities and supporting faster responses.
AI threat detection refers to the use of artificial intelligence to identify situations that may pose risks to people, operations, or infrastructure. Rather than simply storing large volumes of video or sensor data, AI threat detection systems actively analyze this information to generate meaningful insights.
These insights can include automated monitoring, anomaly detection, and early warning signals that alert security teams to potential issues. This approach plays an important role in both cybersecurity and physical security contexts.
The main difference between traditional methods and AI-driven threat detection is how risks are identified. For instance, traditional methods rely on rule-based systems and manual review, which limit their ability to adapt to change.
On the other hand, AI systems are more adaptive. They use data and algorithms to analyze visual information in real time and identify unusual behavior. This helps them identify unknown threats or new threats and support faster incident response, giving security teams more time to act and, in some cases, even before situations escalate.
There are many types of AI threat detection, ranging from AI-driven cybersecurity measures to systems that monitor physical spaces. Different AI techniques support different threat detection needs.
For instance, computer vision is a good option for identifying risks that are visible in the real world. Many potential threats can be observed through cameras, such as unauthorized access to restricted areas, unusual movement, or the presence of objects in unexpected locations.
Specifically, computer vision models like Ultralytics YOLO26 can be used to analyze live video streams to recognize objects and track movement. YOLO26 supports a range of vision tasks, including object detection, object tracking, and instance segmentation.

These capabilities allow systems to identify people, vehicles, or objects of interest, track their movement across scenes, and flag behaviors that deviate from normal patterns. By applying these models to security camera feeds, organizations can move beyond passive monitoring and gain impactful insights into potential risks as they develop.
When deployed at the edge, such systems can operate with low latency and without constant reliance on cloud environments, making them suitable for real-world settings such as factories, warehouses, campuses, and data centers.
Ultralytics YOLO models, such as YOLO26, are designed for real-world applications where speed and consistency are critical. YOLO26’s edge-supported design reduces reliance on complex post-processing pipelines, making it easier to integrate into on-site standard security operations.
Similar to previous YOLO models, Ultralytics YOLO26 is pre-trained on large-scale datasets such as COCO, providing a reliable baseline for recognizing objects such as people, vehicles, and other everyday objects. For threat detection use cases, YOLO26 can be fine-tuned with high-quality application-specific training data to identify people in restricted areas, track movement through secure zones, and flag objects that violate safety rules, such as abandoned items in an airport.
Once trained, the model can generalize to new data, allowing it to maintain reliable detection performance as conditions change. When integrated into larger detection pipelines, its outputs can be used to correlate visual detections with signals from other systems, supporting higher-level analysis like behavioral analysis and improved threat assessment.
Now that we have a better understanding of how vision AI helps identify risks, let’s walk through a few real-world examples of how it is used to detect threats.
In industrial sectors like manufacturing and oil and gas, certain areas within facilities, such as factories, are restricted to authorized personnel only. Often, this is a matter of safety, as these zones may contain hazardous equipment, materials, or processes that require specialized training.
Monitoring access to these areas and ensuring compliance with safety regulations is essential for preventing accidents, protecting assets, and maintaining operational continuity. Generally, such areas are monitored using a combination of human supervision, access control systems, and security cameras.
However, these approaches have limitations. Manual oversight doesn't scale well, access control systems only track entry points, and security cameras typically require constant human attention.
As facilities grow larger and more complex, it becomes increasingly difficult to detect unsafe or unauthorized activity in real time. Vision AI can be a much more reliable approach.
It works by continuously analyzing video feeds to identify safety and security issues. These insights can be integrated into existing intrusion detection workflows, which can trigger automated responses or alerts so human security teams can take immediate action.
For example, a recent study explored how Ultralytics YOLOv8, part of the Ultralytics YOLO model family, can be used to detect prohibited items in restricted areas. In this case, the model was trained to identify the presence of mobile phones in safety-sensitive zones. By learning from application-specific visual data, the system was able to flag policy violations in real time, helping improve compliance and reduce safety risks without increasing the burden on human teams.

In crowded public spaces such as transportation hubs, large events, or busy city centers, understanding how people move and behave is important for maintaining public safety. High crowd density, sudden changes in movement, or individuals falling can quickly create risky situations if they aren’t detected early.
Traditional crowd monitoring systems rely heavily on human operators watching multiple screens, which makes it easy to miss subtle but important changes in crowd behavior. Vision AI improves crowd monitoring by automatically analyzing video feeds from cameras in real time.
Models like YOLO26 can be used to detect and track people in crowded scenes, monitor movement patterns, and identify situations such as falls or individuals remaining on the ground for extended periods. These signals can indicate potential safety issues, especially in dense or fast-moving crowds.

Beyond basic tasks like counting people, vision-based systems can also provide key insights for AI systems that focus on identifying congestion, abnormal crowd flow, or behaviors that deviate from normal patterns. By detecting these early indicators, organizations can respond more quickly to situations that may pose a risk to public safety, supporting timely intervention without requiring constant manual monitoring.
Active construction sites present a range of safety and security risks, as conditions change frequently and workers, vehicles, and heavy equipment move across shared spaces. Unauthorized access to restricted zones, missing personal protective equipment (PPE), or unsafe interactions between workers and machinery can quickly lead to incidents if they aren't identified early.
Vision AI helps address these risks by continuously analyzing video feeds from on-site cameras. Computer vision models such as YOLO26 can detect and track workers across multiple areas while monitoring compliance with safety requirements, including the use of personal protective equipment like helmets or safety vests.
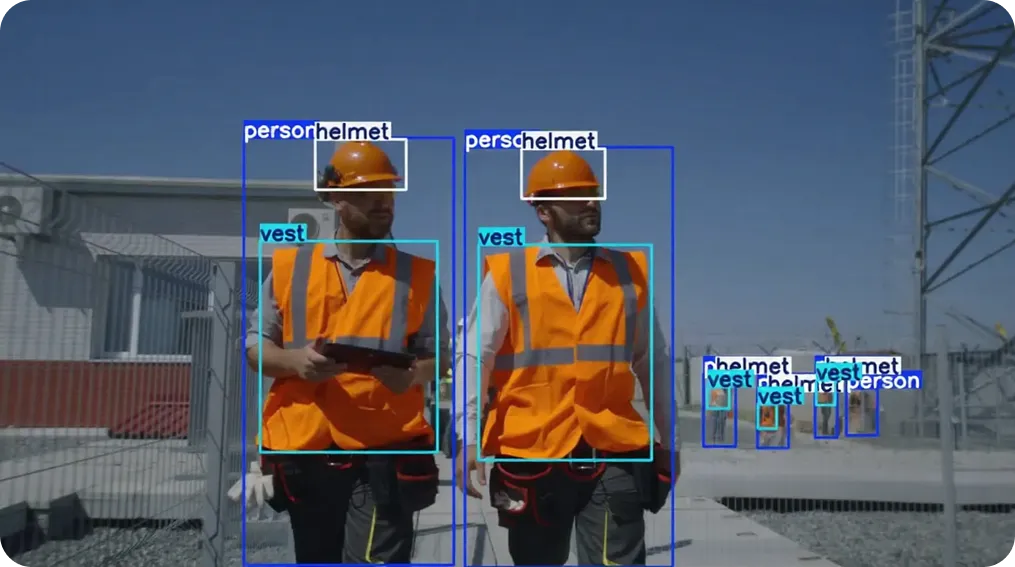
By observing movement patterns and behavior in real time, these systems can flag potential hazards before they escalate. In addition to improving safety oversight, vision-based monitoring reduces reliance on periodic manual checks and supports faster response to unsafe situations.
Here are some key benefits of using vision AI capabilities for threat detection:
While vision AI provides clear advantages with respect to threat detection, it is also important to consider a few limitations. Here are some challenges to keep in mind:
AI-based threat detection combines computer vision and modern security practices to help organizations identify risks earlier and respond more effectively. Models like Ultralytics YOLO enable real-time analysis of visual data, supporting use cases ranging from restricted access monitoring to crowd safety and worker protection. By moving from reactive monitoring to proactive awareness, vision AI helps organizations improve safety in the face of evolving threats, strengthen security operations, and scale threat intelligence across complex environments.
Join our active community and discover innovations such as AI in manufacturing and vision AI in retail. Visit our GitHub repository and get started with computer vision today by checking out our licensing options.

.webp)